Freedom to be secure
SEE WHAT’S ACTUALLY HAPPENING INSIDE YOUR DIGITAL SYSTEMS, THEN CONFIDENTLY DECIDE.
Inside Your Business
Click any object. Every one of these is making decisions on your behalf right now.
You don't lack security.
You have delegated authority.
Every object you clicked is making decisions on your behalf — right now, whether you can see them or not.
Clarity turns change into control."
Click any object in the office to see what decisions it's making for your business — and what you might not know it's doing.
THIS IS FOR YOU IF…
You’re responsible for real decisions, not just execution
You sense something if off in your systems, not just your strategy
Tools, compliance, or training haven’t solved the underlying issue
You don’t want motivation or more controls — you want visibility
You’re ready to stop pretending you don’t see what’s already there
If you’re looking for hype, quick fixes, or performance theater, this probably isn’t a fit.
What I Actually Do
I help leaders and organizations:
Surface how digital systems are making decisions on their behalf
Identify delegated authority and hidden permissions
Clarify trust assumptions and visibility gaps
Reduce noise so judgment improves and recovery accelerates
This work sits between security and governance — where decision authority becomes visible.
Start with Clarity
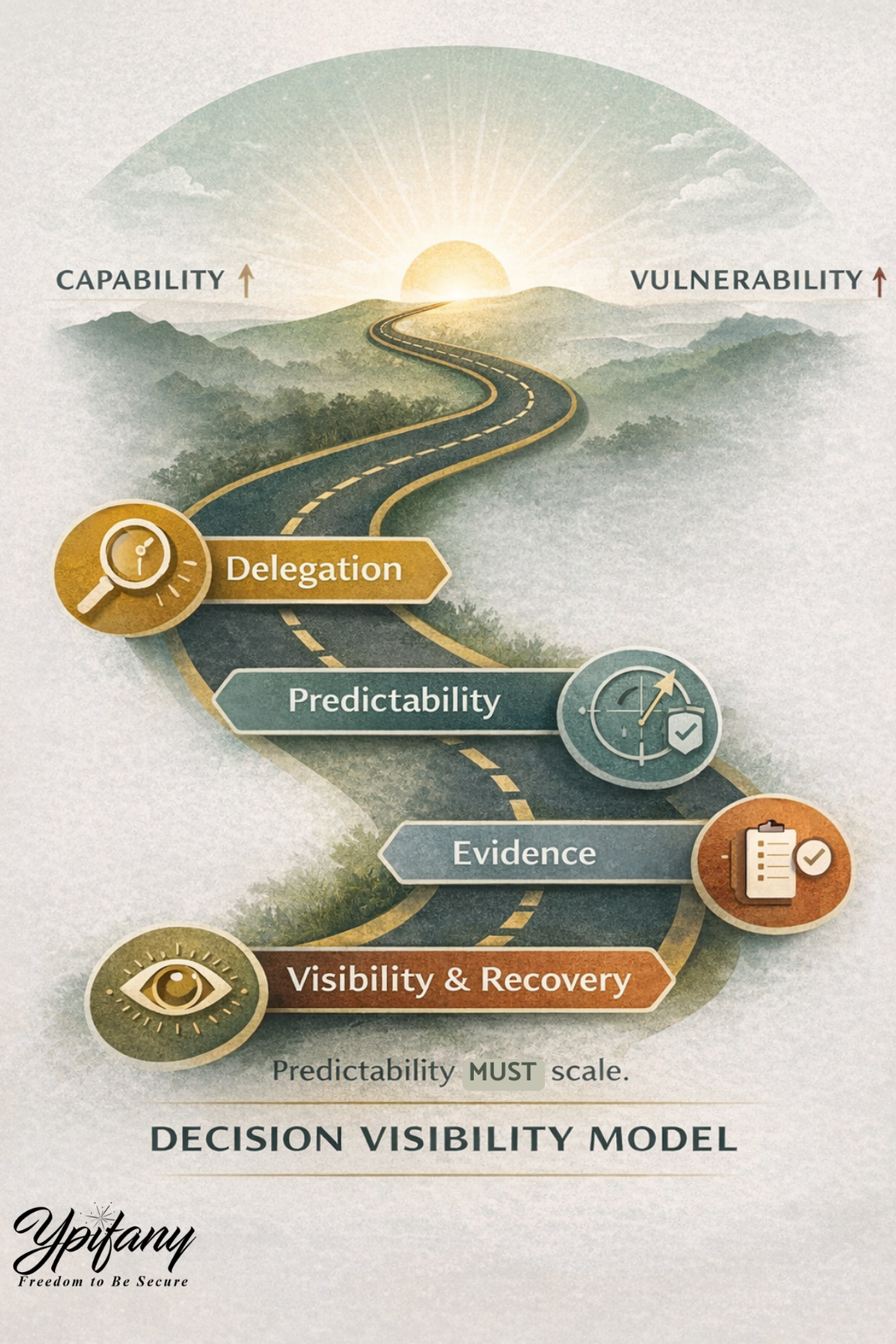
Decision Visibility Intensive
A focused session using the Decision Visibility Model (DVM) ot reveal how delegated systems are functioning and where predictability needs validation.
60–90 minutes
One critical situation or decision system
A completed Decision Visibility Map
This is not coaching or training.
It’s operational clarity.
WORK WITH ME
Ongoing & Project-Based Work
Executive Advisory & Governance Design
For organizations that need ongoing visibility as systems evolve.
Includes:
Delegation and permission drift analysis
Trust validation reviews
Decision visibility briefings
Governance alignment facilitation
Clarity architecture for digital operations
This work begins after an initial Decision Visibility Intensive.
Self-Guided Clarity
Self-Guided Decision Visibility Tools
For independent leaders who want to examine delegation and trust assumptions on their own.
Tools, workbooks, and AI-supported reflection spaces designed to support clarity — not replace judgment.
I’ve supported clarity and decision-making for:
Nonprofits redesigning learning and leadership systems
Cybersecurity and technology teams aligning permissions, people, and processes
Growing companies scaling automation without losing control
Professionals navigating complex responsibility in digital environments
The context, systems, and decisions differ, but the outcome is the same: clearer judgment, greater predictability, and more control.
Re-Imagining Cybersecurity
•
Subscribe to My YouTube Channel PersonCenteredCyber
•
The Power of POA&Ms
•
Subscribe
•
The Ultimate Cyber Range
•
Yes, Length Does Matter. Sometimes
•
Re-Imagining Cybersecurity • Subscribe to My YouTube Channel PersonCenteredCyber • The Power of POA&Ms • Subscribe • The Ultimate Cyber Range • Yes, Length Does Matter. Sometimes •
Ypifany’s Trusted Collaborators